Understanding the Browser-in-Browser (BiB) Attack
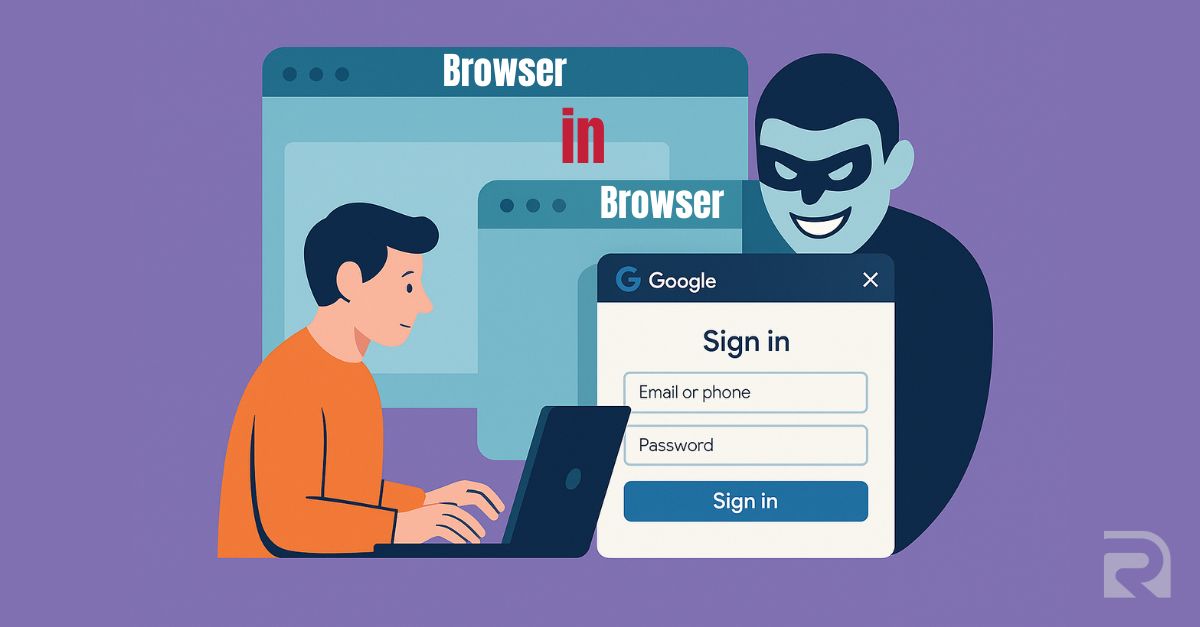
The internet is packed with innovation, but unfortunately, so are the tactics of cyber attackers. One of the newer tricks making waves is the Browser-in-Browser (BiB) attack. Whether you're an everyday user or someone a little more tech-savvy, understanding this attack is key to keeping your accounts and data safe.
Let's dive into what it is, how it works, and how you can defend yourself against it.
What is a Browser-in-Browser (BiB) Attack?
At its core, a Browser-in-Browser attack is a sophisticated form of phishing. Instead of sending you to a fake website, attackers create a fake browser pop-up inside a real website. Imagine you're logging into a service like Google, Microsoft, or Facebook through a pop-up window. It looks real — the branding is spot-on, the URL in the fake address bar looks right, and everything about it feels familiar. But in reality, you're entering your login credentials into a clever imitation designed to steal them. Unlike classic phishing attacks, where the warning signs are often more obvious (like misspelled URLs), BiB attacks play on the trust users place in pop-up login flows.
How Does a Browser-in-Browser Attack Work?
Here's the breakdown: 1. Set the Stage: The attacker creates a website that looks legitimate or hijacks an existing, trusted site. 2. Trigger the Trap: When you attempt to log in or perform a secure action, the site "spawns" a pop-up window that mimics a legitimate login prompt. 3. Fake the Look: Using HTML, CSS, and JavaScript, the attacker designs the pop-up to have all the details you'd expect — even a fake browser address bar and SSL lock icon. 4. Steal the Data: Once you input your username and password, the information is sent directly to the attacker. This attack is effective because it's executed entirely inside the current webpage, meaning your real browser has no idea something malicious is happening. It's essentially a very convincing optical illusion tailored for the web.
Real-World Example:
Security researcher mr.d0x popularized this technique with a demo that faked a Steam login window. It looked almost indistinguishable from the real thing. Attackers have since adapted this technique for services like Google, Microsoft 365, and others.
How to Protect Yourself Against BiB Attacks
The good news? With a bit of awareness and a few good habits, you can dramatically lower your risk. 1. Drag the Window: If a login pop-up appears, try dragging it outside of the main browser window. A real browser pop-up will move independently. A fake BiB window, built inside the webpage, won't. 2. Use a Password Manager: Password managers like Bitwarden, 1Password, or LastPass recognize real websites. They won't autofill your credentials into a fake login form. If your password manager doesn't kick in, that's a red flag. 3. Enable Multi-Factor Authentication (MFA): Even if an attacker steals your password, MFA can block them from accessing your account without a second verification step. 4. Verify URLs Directly: Instead of logging in through pop-ups, open a new tab and go directly to the website yourself. This guarantees you're interacting with the genuine site. 5. Stay Alert for Unusual Behavior: If a login window looks off, behaves strangely, or appears when you weren't expecting it, trust your instincts. Close the window and double-check the website you're on.
Final Thoughts
The Browser-in-Browser attack is a prime example of how cybercriminals evolve their methods to exploit trust and familiarity. But now that you know what to watch for, you're much better equipped to spot the tricks and stay safe.
Remember: cybersecurity isn't just about using the right tools — it's about developing the right habits. Stay cautious, stay informed, and you'll stay one step ahead.