EMMA
Enhanced Management & Monitoring Application
EMMA is REVELSI's custom build application that allows you to easily manage and take control over your entire network infrastructure.
It is an outstanding tool that helps you grow your efficiency at all levels and monitor the performance.
Multivendor Support
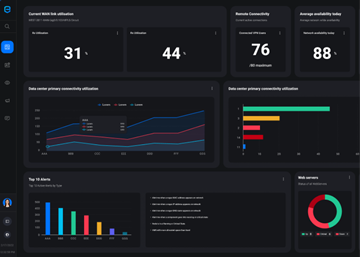
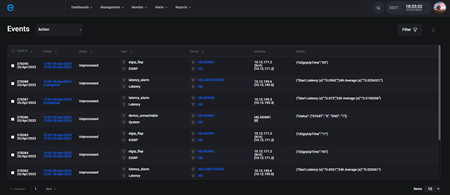
Network Monitoring has never been easier. We collect and log every event that is triggered by any device from your IT infrastructure. We apply complex databases matching algorithms and machine learning processes and what is relevant turns into an alert.
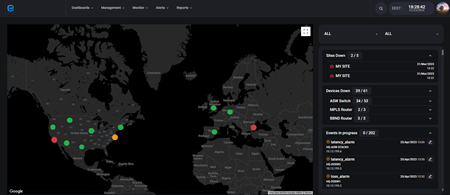
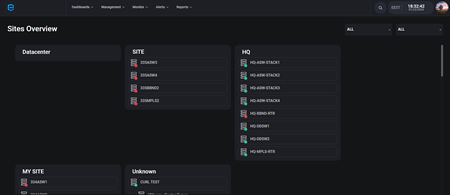
Network Discovery & Mapping
We offer you your network! You will gain visibility of your entire network infrastructure topology. It doesn’t matter if it is on prem, in cloud or is hybrid. As an output, our customers will enjoy a better understanding of the connections between any resources in their network.
Friendly UX
It has been a long time since these applications were used only by tech gurus. We designed EMMA to be used by anyone. It is very intuitive and does not take long to learn. It has customized dashboards for tech guys, for management and administrative personal.
Integration with 3rd party solutions
You’ve got your own ticketing system, or maybe an asset management solution? No problem. EMMA can easily integrate with most of the applications via API calls.
What are the advantages of using a monitoring application for your IT infrastructure?
EMMA is REVELSI's custom build application that allows you to easily manage and take control over your entire network infrastructure. It is an outstanding tool that helps you grow your efficiency at all levels and monitor the performance.
Performance Optimization
and Resource Efficiency
- Resource Allocation
- Capacity Planning
- Cost Savings
Security and Compliance Management
- Enhanced Security
- Historical Analysis
- Compliance Management
- Automated Alerts
User Experience and Productivity
- Improved User Experience
- Remote Management
- Automated Alerts